Due to the recent large-scale cyber attack on the NHS, a lot of people are asking the question ‘what is ransomware?’ So we felt it was best to update our post from last year with some more specific information.
What is Ransomware?
Ransomware is a type of computer software that blocks access to data using encryption technology and displays messages requesting actions (usually payment) to get it back, hence the name ‘ransom’.
The recent NHS attack was made by Wannacryptor 2.0, a type of Locky ransomware. it has also been referred to as Wanna Decryptor 2.0, WCry 2, and WannaCry 2. It has been reported that this piece of malware was first spotted at 9:45 on may 12th, Infections had been found on the NHS network 4 hours later.
How does it spread?
Most ransomware is spread hidden within Word documents, PDFs and other files normally sent via email, or through a secondary infection on computers already affected by viruses that offer a back door for further attacks. Wannacry 2.0 is even more insidious as it can also move between computers in a network by utilising a vulnerability in the Windows operating system (SMBv1 or Server Message Block). Microsoft has already released a catch for this vulnerability which is available through windows update and is detailed on Microsofts website https://support.microsoft.com/en-us/help/4012598/
How Does Ransomware Typically Work?
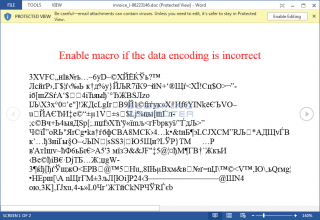
During your busy work day you receive an email with a word document attached, you open it to view the contents and accept the prompt to run macros. The contents of the file will be unexciting, maybe even blank, but the damage has been done. Allowing the file to open and run its macros has already opened the door for Locky (a type of ransomware) and the quite devastating results of its work.
You won’t know anything about it until either you notice the name of your files changing and you not being able to access them, or when it has finished encrypting every file it can get its grubby little hands on and it proudly displays a ransom demand something similar to this:-

A Brief Overview of Locky Ransomware:
Locky is a type of “ransomware” and it targets any office document it can access, be it on your local computer or on your network. this means that it also has the capability to encrypt your network-based backup files.
If you can see it, then Locky can encrypt it!
When started, Locky silently starts getting to work encrypting your files, all your files, saves them under a new file name with a “.locky” extension and removes your original file. This encryption makes them (at present, and for the foreseeable future) impossible to open.
This, of course, can be devastating to any size organisation. Once the files are encrypted by Locky there are only 2 solutions, either to restore from an unaffected backup or to pay the ransom and hope that the file encryption key will be released to you.
How to Minimise the Risk of Ransomware
As always, protection starts with user understanding and education, Malware / Ransomware repeatedly evades AV interception, so the more mindful the end user is of the potential risk the better. Ensure your staff know what ransomware is and how they can prevent it.
Always think before opening an attachment, even if you recognise the source.
Operating systems are continually patched, it is always best practice to keep your operating system and applications up to date to try and ensure no know exploit opportunities exist.
If it subsequently requests access to run macros then definitely think again before allowing macros to run! (Remember our post re spoofed spam emails? spammers can make their emails look like they are coming from a person/source you know and trust.)
If you start losing access to files, or if you see files named xxxxxxxx.locky then alert your administrator straight away, rapid reaction to the signs of an infection can seriously limit the damage of locky (and other viruses/ransomware).
If your backup strategy is to simply make a copy of your files in a different area of your network that you can browse to, it’s time for you to keep your sensitive and important files in a third-party storage or removable offsite as a backup plan in order to recover from ransomware infections.
Steps to Recover From a Ransomware Infection
- Switch off and disconnect any infected computer, do not turn it back on!
- Ensure all staff know about the ransomware and that the machine/machines should not be turned back on under any circumstances, put a big sign on it if required.
- Ensure the source machine is cleaned/reinstalled.
- Scan the rest of your network to try and ensure no other machines are infected.
- As mentioned above, once a file is encrypted and the original deleted, there are only 2 ways of getting that information back, either from your latest unaffected backup or by paying the ransom and hoping you receive the decryption key. By far the best of these 2 alternatives is to recover from backup! But for this to be a viable option you need to have an effective backup solution in place BEFORE you are infected.
- Now is the time to re-assess your backup solution rather than after an infection!
If you would like to talk to us further about this form of ransomware, backup solutions, IT Support or any other technical queries then please get in touch.










