We’re sure you’ll agree when we state that receiving scam & phishing emails are almost a daily occurrence in 2019.
No matter how good your IT system is, cybercriminals are always finding better ways to bypass IT security systems.
As such, email phishing is the new normal.
In this article we’re going to outline the three most common email phishing techniques cybercriminals use so you know what to look out for and are not caught out.
Number 3 on the list is something you should make your colleagues and associates aware of as it’s becoming more common and the chance of you becoming a victim of this attack is highly likely.
1 Spoofing
Email spoofing is when a cyber criminal sends out a mass email to an extensive list of email addresses pretending to be from another sender. An excellent example of this which we see regularly is emails that have been designed to appear to come from well-known technology companies.
These include:
- Microsoft Office 365
- Apple ID Login
- Amazon
- Adobe
Here is a perfect example of a spoofed email from what appears to be Office 365.
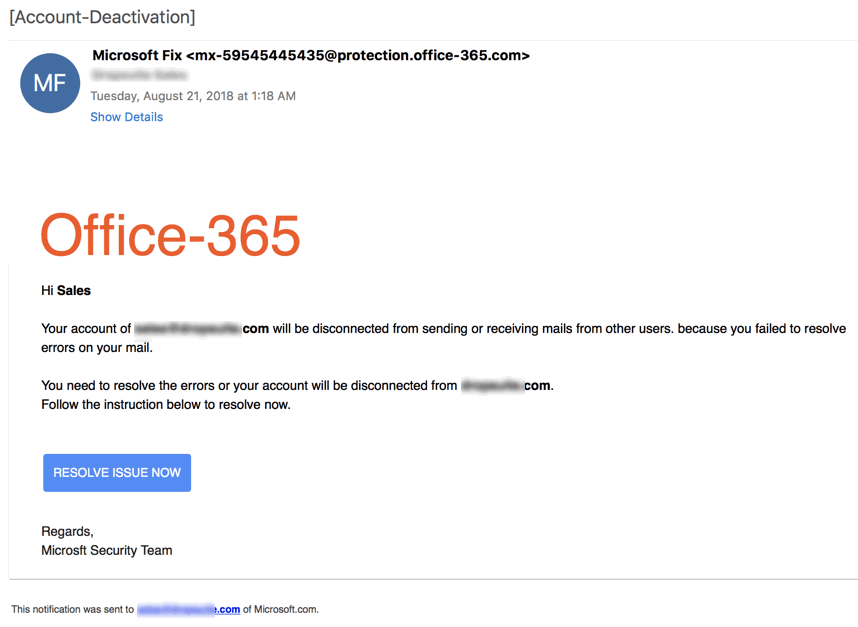
The only way to find out if this email is legitimate or not is to look closely at the sender’s email address.
In the example above the sender is office-365.com, which is not a domain owned by Microsoft.
That’s the first error.
The second is the “resolve issue now” button. Hovering over this link will reveal the URL that the link goes to. It is essential to check all links manually before you click.
2 Cloned Website
A cloned website is usually the 2nd part of a spoofed email. When you click a malicious URL in an email, it will take you to a page that looks like a genuine login screen for an online service you may use.
These cloned websites are easily created by cyber criminals and can be replicated to many website domains.
Again, the only real way to know if it is an official website or not is by checking the URL in the address bar.
If you are in doubt, then it’s worth raising a support ticket with your IT provider or department.
Many online services now attempt to block malicious websites once reported.
Both Google & Microsoft have services which monitor and will warn if you are visiting a malicious website.
This feature does not detect all malicious websites, so again check with your IT Department.
3 Manual Smart Attack
Smart attacks can come in many forms, and it can leave you second-guessing yourself.
An excellent example of a smart attack we recently encountered was an email sent to an HR manager just before payroll was about to be run.
The email in question appeared to be from a senior director in the company instructing the HR manager if he could update his personal bank details for payroll.
The email itself looked legitimate, luckily the HR manager asked the senior director to confirm whether the email was genuine or not and of course he said that it wasn’t.
The attacks are so smart that there’s no real way for software or systems to overcome them. As such, it’s essential that staff are aware of the threats that can come in many forms from email.
If you would like to schedule cyber awareness for your staff, please contact us here.